

This home page is dedicated to my friends and students, with scarce knowledge of Windows and initiating in the use of personal computers who encouraged me to share with them some of my experience of over 2 decades in computer security.

|
WHAT TO DO WHEN A VIRUS IS FOUND ?
|
FIRST COMMANDMENT
SECOND COMMANDMENT
THIRD COMMANDMENT
FOURTH COMMANDMENT
FIFTH COMMANDMENT
SIXTH COMMANDMENT
SEVENTH COMMANDMENT
EIGHTH COMMANDMENT
NINTH COMMANDMENT
TENTH COMMANDMENT
|


WHAT IS A COMPUTER VIRUS ?
Viruses are small strings of program code, ill-intentionally concocted, with the capability of adhering to the code of honest programs that, when innocently executed by the computer operator, may or may not, through annoying interference to normal operations, cause from harmless user irritation to severe damage of the data in a personal computer.
Viruses also may invade certain control areas on the magnetic media of hard disks and diskettes, outside a file, usually in the boot sector, where the computer initialization codes are located.
These initialization codes are set by the FORMAT process. The format process is a necessary operation, that erases all previous data on the hard disk and diskettes, in order to allow a computer to boot up and/or make the magnetic media usable.
The virus code works as a program function that takes hold of important system control areas from where it may replicate copies of itself to contaminate other programs in the active memory and/or programs stored in the magnetic media and/or control areas of hard disks and diskettes.
After some elapsed period of time, once established a certain condition (Date, number of boot-ups etc.) viruses may execute harmful commands to the system vital components. This period of incubations is meant to give the virus time enough to propagate itself among the largest possible number of files in the hard disk and files and/or boot sectors of diskettes used while the computer was infected.
This replicating feature and adherence to other system components capability, similar to real virus in live organisms, granted this replicated string of computer code its meaningful name.
Like any other computer program, a virus is only capable of carrying out any operation WHEN A COPY OF ITS IS RESIDENT IN THE ACTIVE MEMORY. That is what happens when one executes a contaminated program.
INDISPENSABLE COMMENTS FOR UNSKILLED USERS:
ACTIVE MEMORY is the dynamic work area of the processor (CPU=Central Processing Unit). It is dynamic because it is highly changeable according to the CPU instructions and not by the operator's will. It is the only place of the computer system where any operation may be executed. The execution of any operation always requires a PROGRAM. Therefore, a virus is also a program.
PROGRAMS are special codes, different from traditional alphabets, that are composed of instructions to be understood by the CPU to carry out an operation. For instance: To open the Word text editor or to close the Excel spreadsheet or to initialize and to control the rules of a game etc.)
The ACTIVE MEMORY requires electrical power and thus, it IS CLEANED when the computer is shut down. That is why one is necessarily forced to often save one's work to the MAGNETIC MEDIA (HD and diskettes) since these facilities DOES NOT REQUIRE POWER to keep its data safely stored, lest an unexpected power shortage wipes out hours of work.
Furthermore, the computer basic system (Operational System, like Windows) may falter or lock up the entire system, in which case one has to re-boot the computer that will render the MEMORY thoroughly cleaned.
Obviously, files in optical media like the CD-ROM also does not need electric power to be kept stored.

Note the red boxes warnings and the dark green box comment
In the beginning of the computer age, the magnetic media like the hard disk, along with other media like punched cards and paper tapes, were generically called "auxiliary memories".
That is the motive why so many laymen confuse ACTIVE MEMORY (Or Main Memory), today referred to only as "MEMORY", with the hard disk that is a very fast magnetic media of large capacity, simply to store files, that has nothing to do with the MEMORY.
Files may contain DATA (Text, images, sound etc.) called DATA FILE, WORK FILE, IMAGE FILE etc., or PROGRAM codes, called EXECUTABLE FILES.
Any information (data or program) available to the user will always be inside at least one file.
Viruses only contaminate Executable Files or Data Files that partially bear some executable code like the work files produced by the Word text editor, by the Excel spreadsheet and others.

 WHAT IS A MACRO VIRUS ?
WHAT IS A MACRO VIRUS ?
Macro viruses are those who infect programs (that use macro language) only found in restrict environments of applications like the Word text editor, the Excel spreadsheet and others that use the macro language. A macro program cannot be executed outside the application it was meant for.
For instance: A macro program written for Excel is not executable inside Word and vice-versa.These viruses act internally in the work files of the Word text editor that have their names ending in .DOC and in the work files of the Excel spreadsheet that have their names ending in XLs (s=may be other letter).
Macro viruses inhibit vital functions of a Word document or of an Excel spreadsheet. They may, for example, deny the possibility of saving the document or the viruses introduce a password, unknown to the user, that is required to edit the file making it a read-only document.
Like any other virus, worth of its name, the macro virus, once in memory, contaminates all files of the same kind that are opened (loaded in memory) in that session.
That is: Word macro virus contaminates Word documents, Excel macro virus contaminates Excel spreadsheets, although there already are a few macro viruses capable of contaminating both applications work files.
For a macro virus to invade the memory all that is needed is the operator to simply open a contaminated file ended by .DOC (with Word) or .XLS (with Excel). Hence, during that session and sometimes in every subsequent session (depends on the virus), every clean .DOC or .XLS file that is loaded into memory is contaminated as well.
As Word and Excel hold the largest part of the world market for these kind of applications, macro viruses are widely spread.

 WHO WRITES VIRUSES ?
WHO WRITES VIRUSES ?
A virus is a computer program written by people (Hackers) highly skilled in powerful computer languages but with the intention to provoke interference and/or damage to computerized information of others, motivated by:
- Vengeful sabotage against ex-employers.
- Confrontation against organizations, the Establishment and the society in general.
- Personal response to acknowledged challenges among a group.
- Playing Practical Pranks mainly among students.
- Other unclear purposes similar to graffitting walls and monuments.
The word "Hacker" has many meanings in English but, recently it has been applied to those who abuse computer and/or communication means to perpetrate irritating and/or damaging actions to the computerized information or to the assets of other people.
Therefore, those who are able to write a virus code may be considered a hacker, though there are hackers, unable to write a virus code, that invade other people systems to gather information of which he takes advantages either or not with the intention of profiting from it.
Those with intentions of profiting would rather properly be called "pirates".

 WHAT IS A TROJAN HORSE ?
WHAT IS A TROJAN HORSE ?
A Trojan horse is not a virus but a full computer program that does not aggregate itself to other honest programs or magnetic media control areas. They are created to be innocently run by the user to cause immediate or delayed interference with normal operation from a harmless screen message to a complete disruption of the computer system.
Trojan horses belong to a set of damaging programs generically called "worms" that were known only in mainframes, since the late sixties, long before the personal computer age. Viruses appeared in the late seventies but became notorious by the late eighties.
With the widespread Internet use, that linked mainframes to personal computers, the worm threat began to show up also in microcomputers.
The main difference to virus is that worms are not meant to contaminate other programs or magnetic media control areas, but their nasty effects may even be worse than this.
Trojan horses are executable files sent attached to e-mails with palatable names (GirlsNow.Exe, RunMeNow.Com, DontRun.Exe, etc.) or with names of well known files to make the operator to be easily deceived.
These files may also be available at hackers seemingly harmless Internet sites, just for the inadvertent user to download. Once EXECUTED these files will somehow endanger the user system. The download alone will do no harm. The downloaded file HAS TO BE executed for damage to be done.
Common types of worms are:
- Destructive Worms: Logic bombs intended to cause damage to its hosts, like the "Happy99".
- Information Stealers: Worms that keep quiet but monitoring sensitive data (passwords, credit card numbers etc). The monitoring hacker may cause any damage he wishes to your computer or simply simply a junk message, like the "Back Orifice (aka BO)".
- Denial of Service (DoS): Worms that spread bulky spam or many commands in a network like the Internet in order to jam targeted remote servers or computers, like the "Tribal Flood".
- Jokers: Worms whose intent is not to damage but to play a prank on its hosts, like the "Geschenk" that only opens the CD-ROM driver tray, when executed.
ATTENTION
Usually, an antivirus does neither look for nor clean up all kinds of Trojan horses and other types of worms, but those well known worms, like the "Back Orifice" (BO)Trojan horse of which several variants are already in the wild.The motive for this remains in the powerful damage capability of worms, being full programs of their own and not just segments of code like the viruses. Thus, antiviruses restrain themselves to detect but do not completely clean most worms.
For this reason some "Antiworms" softwares (they are not antiviruses) are already being offered as specialized gears in detecting and cleaning only worms, like "The Cleaner" mentioned below.
A shareware version software called "The Cleaner" (about 1.5 Kb) for detecting and removing thousands of Trojan horses may be found at the following site:
Antiworm "The Cleaner"
or at
Antiworm "The Cleaner"
To check for known Trojan horses and other threats go to:
info/virus-news

 WHAT IS A SPARTAN HORSE
WHAT IS A SPARTAN HORSE
The Spartan horse is neither a virus nor a worm. It is a scam in a seemingly innocent home page that exhibits a fake form window asking for personal sensitive user's data. (Ex: User ID and password among other data to test the connection or so)
The wording is quite convincing making the user to believe in common occurrences like line cut-offs or line testings. If the user complies with the request his personal data will be sent to the hacker site where he may use them at will.
One of the first appearances of the Spartan horse occurred in middle 1998, with the simulation of the Dial-Up window that popped up making the user immediately believe his connection with the Internet was interrupted.
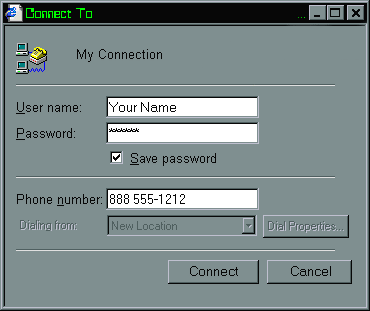
Fake image of the Dial-Up as exhibited by the Spartan Horse
ATTENTION: The greatest danger of this kind of abuse is the fake virtual shopping site that simulates an unsuspected shopping center, with inviting prices. Obviously the user credit card number and related information are promptly asked for. These data go straight to the pirate site for his pleasure and for the user's distress.
RECOMMENDATION FOR CAUTIOUS USERS:
Several abuses through the Internet may be perpetrated by means of Java and ActiveX programming languages used in parts of various sites.
The image of the Dial-Up, for instance, will only be shown by the Spartan horse if the user browser have the Java and JavaScript options enabled, that are the default settings.
Cautious users have them disabled and enables them only when certain of the sheer need of them in a trustworthy site.

 WHAT IS A COMPUTER HOAX ?
WHAT IS A COMPUTER HOAX ?
A Computer Hoax is neither a virus nor a worm nor a scam. It is simply a false alert by e-mail, usually reporting a "terrible virus" whose main objective is to scare novice and inadvertent users and make them innocent tools of spammers (Idiots that jam the Internet channels with junk-mail, chain-letters, pyramids and the like).
Their main goal is always well explicit in every hoax: "Forward this e-mail to all people you have the e-mail addresses..."
To check for known hoaxes go to:

 HOW DOES THE ANTIVIRUS WORK ?
HOW DOES THE ANTIVIRUS WORK ?
An antivirus is composed by several programs that actuates through the following modes:
- 1 - PREVENTION
- 2 - DETECTION
- 3 - RECOVERY
- 4 - EXCLUSION
Each mode requires specific procedures:
1 - PREVENTION (Automatic alert):
During the installation the antivirus should be configured to have its resident part automatically loaded in the memory whenever the computer is turned on. (Example: Program VSHIELD, in the case of the well known VIRUSCAN® product)
In the memory the antivirus acts like a benign "virus" that, occupying the same control areas the mean virus would take hold, alerts the user of and avoids any impending invasion by the virus with its signature listed in the virus name files that comes with the antivirus. (Example: .DAT files of VIRUSCAN®)
Signature is the string of code that digitally identifies a virus.
ATTENTION: Recent viruses, not listed in the virus name files, are not prevented by the antivirus
2 - DETECTION (Scanning):
In this mode the operator runs the scanning program to look for virus in files and control areas on the magnetic media (hard disk and diskettes) according to the supplier's instructions. (Example: Program SCAN of VIRUSCAN®)
The antivirus acts like a detective alerting the user of the already infected files and/or control areas on the magnetic media.
SAME ATTENTION: Recent viruses, not listed in the virus name files are not detected by the antivirus
3 - RECOVERY (Cleaning):
In this mode the operator runs the cleaning program or uses the detector program with added parameters at the command line to clean infected files and/or control areas of the magnetic media, according to the supplier's instructions.(Example: SCAN.EXE and the parameter "/CLEAN" at the command line in the case of the antivirus VIRUSCAN®).
SAME ATTENTION AGAIN: Recent viruses not listed in the virus name files, are not cleaned by the antivirus.
4 - EXCLUSION (Deletion):
There are not antidotes for every known virus. About 1/3 of them do have antidotes. In the case there is not an antidote, the only solution is to delete the infected file.
The exclusion may be carried out:
- (a) Automatically by setting this option in the antivirus while the magnetic media is scanned.
- (b) Manually by the operator outside the antivirus.
It is highly recommended that a list of these infected file be prepared before any exclusion is set out in order to assess the consequences thereof. Therefore the option (b) is preferable.
If the operator identifies the infected file as a work file created by him, he may replace it with a backup, (If available. If not, the work of hours on the file will certainly be lost), but basic systems like the Operational System Windows and main applications, like the Word text editor, the Excel spreadsheet and others, won't necessarily be affected by the exclusion of a file created by the user himself.
On the other hand, if the operator identifies the contaminated file as an executable file (Finals EXE, COM, DLL etc.) or not be able to identify the nature of the infected file, the exclusion will have a high probability of severely hampering basic systems like the Operational System Windows and main applications like the Word text editor, the Excel spreadsheet and others.
In critical situations like this, depending upon the infected file relevance to the system and/or the number of infected files, it oftenly becomes utterly necessary the:
- Re-Installation of applications or
- Re-Installation of the Operational System Windows or
- Hard disk formatting that results in total loss of data and the need for a general re-installation of all softwares.

 WHAT TO DO WHEN A VIRUS IS FOUND ?
WHAT TO DO WHEN A VIRUS IS FOUND ?
The cleaning of viruses in a computer requires a technical ritual that most often is beyond the routine operations of the novice user, not well aware of the viruses malicious antics.
For Instance: IT IS NOT POSSIBLE TO CLEAN A COMPUTER MAGNETIC MEDIA WITH A VIRUS ACTIVE IN THE MEMORY. The virus would re-infect everything again immediately after the "cleaning". Even the antivirus loaded in the memory to perform the cleaning would get contaminated itself.
On account of this, many users, after attempting to clean a computer, get frustrated and wrongly judged the antivirus did not work because the viruses remained as before. In fact the antivirus might have worked even if for fractions of a second before the virus re-infected everything again.
Then, how to perform a cleaning if the virus goes straight to the memory every time the computer is booted up ?
ANSWER: A diskette is used to both start up the computer and run the cleaning programs, not disturbing the infected hard disk in supplying any program code. Thus, the hidden virus in the hard disk cannot get itself into the memory.
This diskette is commonly called "Boot-Up Disk"
Furthermore, it becomes a very hazardous operation for novices to assess the ROM-BIOS setup in order to check the drive boot up sequence so that the diskette drive (A:) is chosen for the boot, prior to the hard disk drive (C:). These are tasks for those familiarized with the description of the above operations only.
For unsavvy users, not well acquainted with such operations, the reasonable procedure to remove viruses is to shut down the computer and look for help with someone who are used to doing it.
Notwithstanding all the discomfort in removing viruses of a computer, the ordeal is not entirely over after the operation is concluded.
The most painstaking but indispensable operations, after removing viruses from a computer, are the ones related to the scanning and cleaning tens, hundreds or maybe thousands of diskettes known or suspected to have been used while the computer was infected.
Never operate an infected computer.
See the motives in the " TENTH COMMANDMENT".

 WHICH ANTIVIRUS IS RECOMMENDED ?
WHICH ANTIVIRUS IS RECOMMENDED ?
VIRUSCAN®: One of the first antivirus in the market since the late eighties when it started with programs to detect and clean a couple of dozen viruses. Today it has some tens of millions subscribers around the world.
It is a set of programs, that constitute the software engine, and a set of files with the signatures (DAT files) of over 50.000 viruses. The engine is updated every 3 or 4 months but the DAT files, with approximately from 100 to 300 new signatures, are updated weekly and posted at the supplier Internet site.
Both the software engine and DAT files may be downloaded free for trial, but the engine in this case, usually is an out of date version. The price for the Viruscan alone is about a few dozens of US dollars rendering it the best cost effective antivirus in the market. The DAT files are always free for all.
Viruscan® is a product of Networks Association Inc. that incorporated MacAfee Associates, the previous developer. It may be found in several languages.
More Information: http://www.nai.com
NORTON ANTIVIRUS®: One of the most well known antivirus in the market and widespreadly used all over the world.
It is more expensive than Viruscan® costing some dozens of US dollars. It has many interface windows and wizard screens to guide the user.
Norton Antivirus® is much more advertised than the others by Symantec Corp. and it is also found in several languages.
More Information: http://www.symantec.com
F-PROT® (Currently F-SECURE®): One of the most recent successful antivirus, similar to VIRUSCAN® that introduced the heuristic method by searching, not for viruses themselves but, for traces left by them in the system, as an option for the user to chose as an alternative to the traditional comparative method.
However the catch is that some honest, though few, programs leave similar traces and so the method is never conclusive. Its messages always begins with "File possibly infected..".
The advantage of the heuristic method is the possibility of somehow checking the presence of new virus not yet cataloged in the virus signature files used by the comparative method.
The recent versions of VIRUSCAN® and NORTON ANTIVIRUS® also present the heuristic method as an option.
The price is comparable to the NORTON ANTIVIRUS®
Produced by Datafellows Inc. it is found in several languages.
More Information: http://www.www.datafellows.com

 HOW TO REDUCE THE THREAT OF VIRUS INFECTION ?
HOW TO REDUCE THE THREAT OF VIRUS INFECTION ?
![]()
.