|
PURPOSE OF CRACKING THE passwd
Traditionally stated, the purpose of hacking a UNIX is: to "get to ROOT."
This refers to the ROOT account that every UNIX system has as part of it's
Operating system. The ROOT is a 'Trusted User' account, THE most powerful
account on a UNIX. If you can hack a ROOT you can utilize or exploit every
function a UNIX is capable of. But to get to "ROOT" you have to have
somewhere to start. For the purposes of this file, that somewhere is with
the 'passwd' file.
WHAT'S THE passwd?
'passwd' is the common name of the file in which user account information is
stored on a UNIX system. You might consider it a comprehensive users list.
The file contains the information for an accounts USERNAME, PASSWORD, USER
NUMBER, GROUP, GECOS, HOME DIRECTORY, and SHELL. A single entry of a passwd
file entry might look like this:

Now take a look at the PASSWORD in this entry: 8d34jSjs73hsb. This is, in
fact, NOT the password. It is, instead, the encrypted equivalent TO the
password. As part of the UNIX Account Registration process, when a User
designates a password, the UNIX takes the password, and (*this is
important*) uses the other information from the account to generate an
encrypted equivalent to the actual password. Why? Because as part of the
UNIX operating system, users MUST have access to the 'passwd' file to be
able to login. But if anyone who has an account can access the 'passwd'
file, they can also see what everyone else's Password is. So, UNIX's
security against this is to encrypt the password entry for each users
account so that noone else will know what anyone elses password is.
Unfortunaley/fortunatley (depending on who you are) the algorithm UNIX uses
to perform this encryption has been known to Hackers for sometime. And so if
you can see this:

GUESSING THE PASSWORD
First a UNIX 'passwd' file cracker takes an encrypted password equivalent
(i.e.: 8d34jSjs73hsb) from an account entry in a UNIX 'passwd' file and
holds it to be used as a Reference. From whichever account entry the
encrypted equivalent was pulled, is the particular account the 'passwd' file
cracker will attempt to crack at that time.
Next the 'passwd' file cracker goes through a process of "guessing". In this
process a single word is pulled from a Dictionary file (more on Dictionaries
later), encrypted utilizing the UNIX encryption algorithm (the one all us
hackers know about), and compared, checking to see if the derived encrypted
word matches the encrypted password equivalent used as a Reference.
If the encrypted word matches the Reference, the 'passwd' file cracker
considers it an accurate guess, it then logs the information, and moves on
to the next account. If the two do not match, the 'passwd' file cracker
pulls another word from the Dictionary file and goes through the guessing
process again. If the 'passwd' file cracker goes through every word in a
Dictionary file and never matches the Reference, the entry is skipped, and
the cracker moves on to the next account.
Now, as complicated as this may seem, it is all a relativley easy task for a
computer. As such, UNIX 'passwd' files are cracked on a regular basis. As a
result of this a number of security and other measures now (potentially)
exist to prevent unauthorized persons from accessing a UNIXes'passwd' file.
This is the topic of the next section. To this point you should understand
why UNIXes are hacked (to get to ROOT) and understand a little about
'passwd' files and their role in UNIX hacking. Got it?
GOT IT, NOW WHAT?
Ok, at this point you should be ready to try and find a UNIX 'passwd' file
to crack, right? Wrong. You still have a couple of minor, requisite tasks to
perform. First, (obviously) you'll need to find a UNIX to hack. In most
cases, you've already got one in mind, but just in case you don't we'll take
a look at a few. Also, once you've found a UNIX to hack, you'll need an
account on that UNIX. There's no way to steal the 'passwd' file from a UNIX
without first having an account on it (not true, you can always get a
'passwd' file from someone else, but ignore this because I'm contradicting
myself). Once you've accomplished your requisites you can start trying to
steal the 'passwd' file.
Step 1. Finding a UNIX to Hack
------------------------
Seeing as how you're reading this file you probably already have a UNIX in
mind. But, for the sake of clarity, heres what a common UNIX login screen
looks like:
Ultrx v4.3 (rev .44)
login:
Other UNIX machines are: System V, BSD, Xenix, and AIX. Look for these names
to be somewhere in the login screen. Knowing what type of UNIX you're using
will aid you in hacking it.
Step 2. An account to start with
--------------------------
If you already have a UNIX account go to Step 3. If you do not already have
an account, you need to get one. Either: trade for one, trash for one, get a
legitimate one, or hack one out by hand. The first three options are
probably the easiest. You can trade for UNIX accounts on IRC channels #hack
or #phreak. You can trash for accounts in dumpsters and trashcans at most
Colleges or Universities. You can buy legitimate accounts from any one of
the rapidly increasing number of Internet Service Providers (they almost all
use UNIX). But, of coure, as well know you're a hacker, and the only hing
you wanna do is Hack an account. So be it. Here's a list of UNIX defaults.
*NOTE* These are NON-PASSWORDED accounts. They are common on System V, BSD,
Xenix, and AiX. "These defaults are included in standard setup on various
machines so the Sysadmin can log on for the first time." In some instances,
negligent Admins will forget to change or delete these accounts. If so,
you've got an account to start with. Remember, these are NON-PASSWORDED so
if they work you shouldn't be prompted for a password. If a password is
prompted for, try using the Account name for the password as well.
[Stolen from CoTNo #01]
|
root | bin | adm | |
makefsys | sysadm | sys | |
mountfsys | rje | sync | |
umountfsys | tty | nobody | |
checkfsys | somebody | setup | |
lp | powerdown | ingres | |
dptp | general | guest | |
daemon | gsa | user | |
trouble | games | help | |
nuucp | public | unix | |
uucp | test | admin | |
student | standard | pub | |
field | demo | batch | |
visitor | listen | network | |
uuhelp | usenet | sysinfo | |
cron | console | sysbin | |
who | root2 | startup | |
shutdown | ncrm | new |
Step 3. Stealing the passwd file
-------------------------
Once you've got your UNIX accpunt you can ATTEMPT to steal the 'passwd' file
from it. I emphasize ATTEMPT because the 'passwd' file can be protected in a
number of ways, or located in a number of different places. We will explore
some common methods of exploiting the 'passwd' file.
-Common UNIX Hack-
This is probably THE easiest and most common UNIX hack. ogin in to your
account and try typing this at the prompt:

'cat' is short for concatenate, a command used for reading and displaying
files in standard output. '/etc' is the common directory for the password
file on older UNIXes. 'passwd' is the common password filename on UNIXes. If
you entered: cat /etc/passwd and got a listing that looks like this
(abbreviated):

...then congrats! You've succesfully listed out (stolen) your first 'passwd'
file. *Buffer* the entire contents to a text file, save it and find a password cracker.
If you got a listing that looks like this:

or:

or you got:
cat: cannot open /etc/passwd
Then the UNIX you are on is utilizing some other form of protection or may
be using a different 'passwd'-ing process. Keep reading.
-AIX-
On AIX systems, an UNIX variation, the 'passwd' file is in a different
place. On an AIX type:
booya> cat /etc/security/passwd
If this lists out a 'passwd' file with the (encrypted) password intact, then
you've succesfully listed out (stolen) your first 'passwd' file. *Buffer*
the entire contents to a text file and save it, and use your password cracker.
If not, keep reading.
-NIS/yp-
Some UNIXes use a system called Yellow Pages [taken from #hack/alt.2600 FAQ
beta .013]:
"NIS (Network Information System) is the current name for what was once
known as yp (Yellow Pages). The purpose for NIS is to allow many
machines on a network to share configuration information, including
password data. NIS IS NOT DESIGNED TO PROMOTE SYSTEM SECURITY. If
your system uses NIS you will have a very short /etc/passwd file that
includes a line that looks like this:
+::0:0:::
"To view the real password type this command:"
booya> ypcat passwd
If 'ypcat' lists a password file with the (encrypted) password still intact,
*buffer* the entire contents and go to password cracker, if not, keep reading.
-Password Shadowing-
Some systems use what is called password shadowing [again, taken from
#hack/alt.2600 FAQ beta .013]:
"Password shadowing is a security system where the encrypted password
field of /etc/passwd is replaced with a special token and the
encrypted password is stored in a separate file which is not readable
by normal system users.
"To defeat password shadowing on many (but not all) systems, write a
program that uses successive calls to getpwent() to obtain the
password file.
"Example:
-------------------------------------------------------------CUT HERE
#include >pwd.h>
main()
{
struct passwd *p;
while(p=getpwent())
printf("%s:%s:%d:%d:%s:%s:%s\n", p->pw_name, p->pw_passwd,
p->pw_uid, p->pw_gid, p->pw_gecos, p->pw_dir, p->pw_shell);
}
-------------------------------------------------------------CUT HERE
Now then, for those you who are unfamiliar with UNIX scripts and/or their
implementation, follow these directions:
First Copy the above script (not including the CUT HEREs) into a Text
file and save it as 'getp.c'. Next Login to your UNIX account and create a
directory called 'executables'. (At the prompt) Type:

Now, use Fetch or some other FTP client to FTP into your account and
Upload 'getp.c' into the directory 'executables'. Once you've done this,
login to your account, and goto the 'executables' directory:

Type 'ls' to List the directory to make sure the file is there. If it is
you can attempt to compile the 'getp.c' script. Almost all UNIX boxes
have Compilers, it's just a matter of whether or not you have acces TO
the Compiler. Typically you do. at the UNIX prompt Type:

If you don't get an error you should be left with a file named 'a.out'.
Type:
booya> a.out
If you get a listing with the (encrypted) password intact, *buffer* the
contents to a text file and use your password cracker, if not, keep readin'.
If you got an error when you tried to compile the 'getp.c' script: 'cc:
Command not found' then you either don't have that compiler or you don't
have access to it. In either case, try compiling with the GNU C Compiler:

Again, you should be left with a file named 'a.out'. At the UNIX prompt
type: a.out. If you get a password file with the (encrypted) password file
intact, *buffer* the entire contents and your password cracker. If not, keep
reading.
-Last Resorts-
In some cases none of the above listed attacks may work. It might be because
you're running a newer version of UNIX like SunOS v5.4. Also it, may just be
that you don't have permissions to access the 'passwd' file for whatever
reason. In the case of SunOs v5.4, v5.4 doesn't have those helpful v4.1.x
bugs so well documented in the CERT Advicories. In this case your best bet
may be to go pick up a book on UNIX (so you can know what you're doing), and
then goto the Bugtraq Archives:
http://www.eecs.nwu.edu/~jmyers/bugtraq/search.html
...and do a search for 'SunOS 5.4'. Any vulnerabilities in 5.4 (or any other
system for that matter) may be found there.
In cases where you just don't have access to the 'passwd' file for whatever
reason, you might try the 'Dumb User' Hack: Login to a UNIX using whatever
account you have. Once you're logged in, at the prompt type:
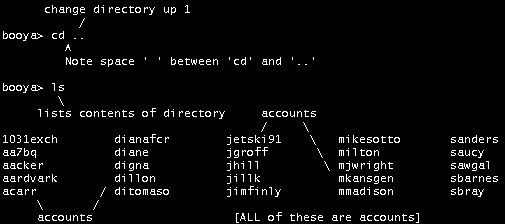
[etc...]
What this process does is give you the names of all the common accounts on
the UNIX you're on. Buffer this list and print it out. Exit the UNIX (type:
exit) and try to Hack back using these accounts with the Account name as the
password. i.e.:
-UNIX(r) System V Release 4.0 (arthur)-

This is the 'Dumb User' Hack. Because a user was 'dumb' enough use his
account name for his password, it was easily hacked, and now that dummy's
account is your's. If the Dumb User's account has more privileges than
yours (i.e. Permission to read the 'passwd' file), go back through the
previously described methods and attempt to get the 'passwd' file. If the
account has no greater privileges, keep the account for later trading on
#hack and try and hack another account with more privileges.
If you've tried everything and you still haven't succeed in stealing a
'passwd' file, goto bed and thank God you don't have more troubles in life.
|