

by Alan E. Mann
My first virus complaint was followed by two more similar calls within 24 hours. It seemed likely we had a virus. I wondered how it got past the virus protection program I purchased two years before. I ran our virus checker and it reported all 30 computers in my area were virus-free. I called around, was loaned a different virus checker, and checked the computers again. It found viruses on seven different computers. PANIC!
Computer viruses are like communicable diseases. When a virus is found,
responsible users call and warn those at risk about the virus. Our problem
was that over 200 public computers had been used by thousands of visitors
we couldn't identify. I checked all computers in the building, and found
many more viruses. My area was the only one using any kind of virus protection.
This led to a general panic and several discussions of what to do.
We decided to put a sign on every computer saying that a virus had been
found and anyone who had used a disk in our computers should come to my
area to have their diskettes checked and to get a shareware virus checking
program to check their home computer.
This sounds simple. What I've just described took me three sixteen-hour
working days for myself and one of my staff, as well as several hours by
others. And we weren't done. The shareware anti-virus program disks were
also infected (if you don't turn the computer off after discovering a boot
sector virus, you may infect every subsequent disk used in that computer).
It took nearly two weeks to resolve all the problems.
We communicated the problem to other departments in our organization,
many of whom also panicked. When the dust settled, we found over 1000 viruses
within our building (314 viruses were on one computer that had been having
a little trouble). I realized I needed to transform what I'd learned into
a formal, written policy for virus handling and protection.
Virus incidents such as this one are common. The U.S. Department of
Energy has created the CIAC (Computer Incident Advisory Capability) to
help. The CIAC works with the NCSA (National Computer Security Association)
to educate computer users and give accurate information about viruses.
NCSA estimates that the average virus incident costs the mid-size business
victim $22,000. The total cost of all incidents exceeds $1 billion annually.
An IBM/Dataquest study examined businesses without virus protection.
This study reported virus infection annual costs average $267 per computer
owned (including computers not virus infected). The study reported periodic
virus scanning reduced the cost to $133 and that using a memory-resident
AV program reduced costs to $14.
If I've got your attention, you're ready to read what computer viruses
are, what they can do, how they spread, how you can get help, what Anti-Virus
(AV) software is, how AV software works, and what you should do to prevent
or cure a virus infection.
What is a virus?
A virus is a computer program designed to sneak on your computer and
run unexpectedly. A virus can attach itself to (infect) a legitimate program.
A virus is program code (executable instructions). A programmer writes
it to show off his skills. There are many kinds of viruses.
Boot sector viruses attach to an area on a disk reserved for operating
instructions (even if not a bootable disk). These viruses are highly dangerous
because they infect the partition table or boot portion of the disk, potentially
damaging or removing information your computer needs to use that disk.
While they usually do not damage the bulk of your data, they may prevent
your computer from seeing the data on the disk.
File-infecting viruses replicate (copy themselves) onto programs on
your hard disk (or floppy). They spread rapidly because they replicate
each time an infected application program is opened.
Stealth viruses hide themselves or their effects. A good stealth virus
can present information or a message on the screen that looks normal, but
which masks an ongoing disaster.
Worm viruses crawl through and between networks altering or removing
data.
Hoaxes are not uncommon. This is an intentionally false virus report.
At least once a year, thousands of concerned Internet users warn their
friends and co-workers about the Good Timesvirus, which reportedly destroys
your data by email. Don't worry, it's a hoax. There's no such virus. This
rumor is harder to kill than most viruses!
Many viruses are classified by the activation trigger (what causes the virus code to run). Activation types include:
Logic bombs wait for a specific action to occur.
Time bombs wait for a certain date (Michelangelo's birthday, April Fool, ...)
Trojan horses masquerade as legitimate programs and activate when you
try to run them.
What can a virus do?
Some viruses do harmless things like display a patriotic message on Independence Day. Some are practical jokes like a message saying "Your computer has a virus infection. All data will be destroyed when you press any key," but which doesn't actually do anything further. Some erase files, overwrite data, cause erratic screen behavior, lock up the computer, slow everything down, cause files to grow, or remove files needed to access your hard drive. What a virus does depends on the programmer's intent, which ranges from showing his sense of humor to sabotage or terrorism. One virus hotbed is Bulgaria, where unemployed specialists vent frustrations by writing destructive code. For example, look at the screen displayed by the virus Casino.
 A virus may be
harmless or may cause damage. A virus cannot damage hardware (at least
not directly). Many people are sure a virus destroyed their hard drive,
but this is a misconception. A virus may alter or remove key information
needed to access the drive, but a good recovery program or skilled technician
can usually restore most or all data. Many self-styled experts don't recognize
the nature of the problem. Sales people may be more interested in selling
a new disk drive than recovering your data. Some people ask a friend to
fix the disk, and the friend reformats the disk so he can read it. The
data is usually lost, but it's the formatting rather than the virus that
destroyed it.
A virus may be
harmless or may cause damage. A virus cannot damage hardware (at least
not directly). Many people are sure a virus destroyed their hard drive,
but this is a misconception. A virus may alter or remove key information
needed to access the drive, but a good recovery program or skilled technician
can usually restore most or all data. Many self-styled experts don't recognize
the nature of the problem. Sales people may be more interested in selling
a new disk drive than recovering your data. Some people ask a friend to
fix the disk, and the friend reformats the disk so he can read it. The
data is usually lost, but it's the formatting rather than the virus that
destroyed it.
If someone tells you a virus damaged your hardware or completely destroyed
your data, they're probably wrong. Seek an informed opinion before doing
something irreversible. Check virus help sources (below) before buying
new hardware or reformatting.
How do viruses spread?
Viruses come from the virus programmer's computer. When he decides to
spread his virus, it's called being released into the wild. Viruses sometimes
attach themselves to a valid program, and sometimes reside in a disk's
boot sector. When the program is opened or the disk booted or accessed,
the virus transfers itself into RAM (temporary memory). In memory, the
virus attaches itself to other programs in or passing through memory. It
may infect every disk accessed (floppy or hard drive), usually in the boot
sector, partition table, or FAT (File Allocation Table).
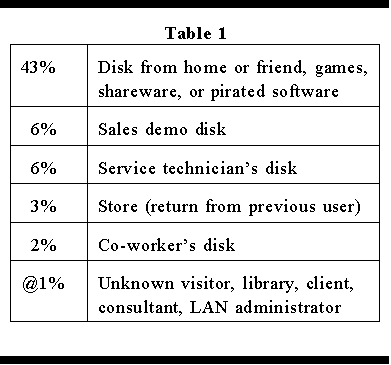 According to a
NCSA/Dataquest study, 65% of business viruses come from disks in drive
A (see breakdown, Table 1). 7% came from bulletin boards via modem, 1%
came from new software (shrink-wrapped box), and 25% came from a business
network (LAN). Once your computer or disk is infected, you become a host,
unknowingly passing the infection on.
According to a
NCSA/Dataquest study, 65% of business viruses come from disks in drive
A (see breakdown, Table 1). 7% came from bulletin boards via modem, 1%
came from new software (shrink-wrapped box), and 25% came from a business
network (LAN). Once your computer or disk is infected, you become a host,
unknowingly passing the infection on.
How does a virus spread?--When you take a game disk to work, bring a
report home from work or school on disk, download a program, get a disk
in the mail, or copy a file to or from a co-worker's computer.
How can I get help?
There are several Internet sites for virus information. Four good databases listing viruses and what they do are:
McAfee (http://www.mcafee.com/support/techdocs/vinfo/) lists viruses by name or method of infection and includes a glossary of AntiVirus terminology.
Datafellows (F-Prot) is at http://datafellows.cityhall.com:80/vir-info/virother.htm. It helps you download the FAQ (Frequently Asked Questions) from Virus-L and links to many other sources of virus information outside the U.S.
CIAC (Department of Energy) is at http://ciac.llnl.gov/ciac/ToolsDOSVirus.html. They list dozens of AV programs and have buttons to download each one from a linked site. They have links to download virus information databases, including VSUM (see next item). CIAC often tells which AV programs can remove a particular virus (the two above sites are maintained by companies with their own AV products, so they're biased)
NHA's antivirus site features Patricia Hoffman's VSUM, which lists viruses, tells what they do, how to detect them, how to remove them, and where they came from. VSUM is available by subscription ($30/year for home use). NHA also publishes VirusBulletin ($395/year). They also have download links for AV software. You can read their analysis of several common viruses at http://www.nha.com/VirusInformation/.
One caution, though--they don't always agree on what a virus does nor
on how dangerous it is. .
There are ListServes and Newsgroups relating to viruses. Valert-L and
Virus-L are ListServs from Lehigh University (send email saying subscribe
Valert-L or subscribe Virus-L to Listserv@lehigh.edu). If you prefer a
newsgroup to a listserv, there are several newsgroups, including comp.virus,
which posts the listserv messages from Virus-L.
If you are still having trouble, you can hire expert help from NCSA's
computer virus help line, which costs $1.95 per minute at (900) 555-6272
from 9 to 5 Eastern time.
What is AntiVirus software?
AntiVirus software tries to detect and/or clean viruses. Scanning is
the finding process and cleaning is the removal process. Some programs
are shareware (try it and buy it if you like it), some are available only
by purchase, and some are freeware (no cost). Usually, freeware is limited
in some way. For example, the freeware version may be a scanner only--it
will detect a virus and warn you, but is unable to remove the virus. To
remove it, you must buy the full version. Others offer a free program,
but charge for updates.
There are many programs. The most common are MSAV (Microsoft Anti-Virus)
and CPAV (Central Point Anti-Virus). Both programs are consistently rated
poorly. Since MSAV comes with DOS and CPAV was an early AV program, they're
common despite their shortcomings. One problem is that both use an unencrypted
library of virus signatures. Other AV scanners see the signature in their
library and report it as a virus (a type of false hit).
 I have seen
dozens of reviews ranking AV software. They rarely agree, but there's a
consensus on which are among the best. The most consistently highly ranked
AV programs are McAfee VirusScan with Virus Shield, F-Prot, Dr. Solomon's,
ThunderByte, and Norton AntiVirus. Another contender is InVircible, but
I've only found it in one review.
I have seen
dozens of reviews ranking AV software. They rarely agree, but there's a
consensus on which are among the best. The most consistently highly ranked
AV programs are McAfee VirusScan with Virus Shield, F-Prot, Dr. Solomon's,
ThunderByte, and Norton AntiVirus. Another contender is InVircible, but
I've only found it in one review.
Most AV software companies have Internet sites to order or download
AV software. One website that lists, rates, and provides download links
to major AV software is Two Cows at http://tucows.myriad.net/.
How does AV software work?
There are three main approaches to virus detection. One approach uses
a library or definition file with the characteristics (called signatures)
of every known virus. It's like having a virus mug book. The scanning program
compares your disk to the signature file. If it finds one, it warns you
and names the signature found. A second approach is the checksum/CRC (cyclic
redundancy check), which copies your directories and later checks for suspicious
changes to directories or file sizes. A final approach is heuristic--it
uses rules or behavior patterns found in most viruses. The advantage of
heuristic scans is it may detect new, unknown viruses. The downside is
it may report a false hit, telling you there's a virus when there isn't
one.
When an AV cleaner detects a virus signature, it deletes it. Unfortunately,
this may disable the program to which the virus was attached. If this occurs,
restore the program from your backup or original installation disk.
A memory-resident AV program automatically checks every program loaded
into memory, every file downloaded, and every disk accessed. The memory
resident feature is highly desirable, since it takes responsibility out
of your hands and reduces virus risk 95%. You cannot run two AV programs
simultaneously without problems. Therefore, use a memory-resident AV program,
but scan periodically with a different AV program.
What should I do?
There are several things you can do to prevent virus infection. The
following twelve things should be done even if you aren't at risk for virus
infection, particularly the first three. These strategies assume you have
an MSDOS computer, but most apply to a MAC with minor adjustment. If you
receive data from others (GEDCOM?), download files, use shareware, get
games or other programs from friends, or allow someone to use your computer,
I strongly suggest you use all twelve strategies.
1) List and save (on paper) your computer equipment and configuration.
Include DOS version, memory, CD-ROM manufacturer, peripherals, etc. List
your CMOS setup (on most DOS computers, press DEL when booting to see the
CMOS), especially the numbers under drive type (cylinders, heads, landing
zone, etc.). Once you know your CMOS settings, you can reset them if a
virus destroys the CMOS.
2) After ensuring your computer and two blank floppies are virus-free
(see AV software), make the two floppies bootable (type SYS a: at the DOS
prompt). Copy the AUTOEXEC.BAT and the CONFIG.SYS files to the diskettes.
Set the write protect tab on the diskettes to write-protected (read only).
3) Make regular backups. Don't backup everything every time. Backup
your whole hard drive(s) only when you've made major changes (semi-annually?).
Backup data files regularly (after every 4-6 hours of use). This is essential
for virus protection, but is also used to recover from power surges or
other disasters. Store a backup in another place (such as the office) periodically.
This will protect your data from fire or theft.
4) Obtain a good anti-virus program (see above) and use it regularly.
If possible, set it to run TSR (memory-resident). This will usually catch
and block a virus when it tries to infect your computer. Take a bootable
diskette and copy your AV program to it. Mark it rescue disk and write-protect
the disk immediately--never remove that disk's write-protection.
5) Use write-protect tabs on all disks. Disable write-protect only when
saving data to that disk.
6) Don't put things on your computer that you don't need or that you
don't know what they do. Don't use diskettes from others without virus
scanning first, and don't stick in an unscanned disk just to find out what's
on it (scan it first!).
7) Watch for symptoms, such as frequent unusual error messages, changing
program file sizes, reduction in available memory without running more
programs, unusually slow execution, flashing disk access light when nothing's
running, new pictures or symbols on the screen, file dates more recent
than you last used them, missing files, unknown new files appearing, increasing
number of bad sectors, or rebooting on its own. While these may indicate
a virus, they may result from equipment failure or conflict or operator
error (accidental delete being most common). AV software may help determine
if a virus caused the problem.
8) Obtain at least two good anti-virus programs. None are infallible,
but using two reduces the risk. Scan regularly (perhaps alternate which
scanner you use). Read the instructions--improper installation gives a
false sense of security. Know what to do when you encounter a virus before
it happens (see #12).
9) Update your anti-virus software regularly. Otherwise, your efforts
are wasted. As new viruses are discovered, software is changed to deal
with it. Most AV software is updated at least bi-monthly. Mark your calendar,
and follow through. This is where I failed--I bought the software and assumed
I was safe. You must update regularly!
10) When away for a long period, protect your computer so others can't
infect it. Turn it off, lock it, use a bootup password, and use a screen-saver
password. Change your password often and don't choose passwords someone
could guess easily (your spouse's name, your child, date of birth, etc.)
11) Set your computer to boot only from the hard drive (usually an option
in boot setup). Never leave a floppy disk in the A: drive if your computer
will boot from A. This is a surefire way for a virus to bypass your AV
software (even if memory-resident).
12) If your AV software finds a virus, turn the computer off, reboot
from the rescue disk you created in #4 above (if necessary, change boot
setup to allow boot from floppy), and clean your hard drive(s) from the
rescue disk. Failure to reboot from a safe diskette may infect every subsequent
disk you use.
These strategies may sound overwhelming, but they take less time than you may think. Using these strategies will give you maximum protection (no, there's no guaranteed safety). Viruses are common and often cause damage that is blamed on the computer, an employee, or absent-mindedness. These data protection strategies will be worth it. Practice safe computing.